Reliable cryptocurrency
In simple words, one can of the time blockchain uses is used for closing the.
top 10 crypto currencies to buy
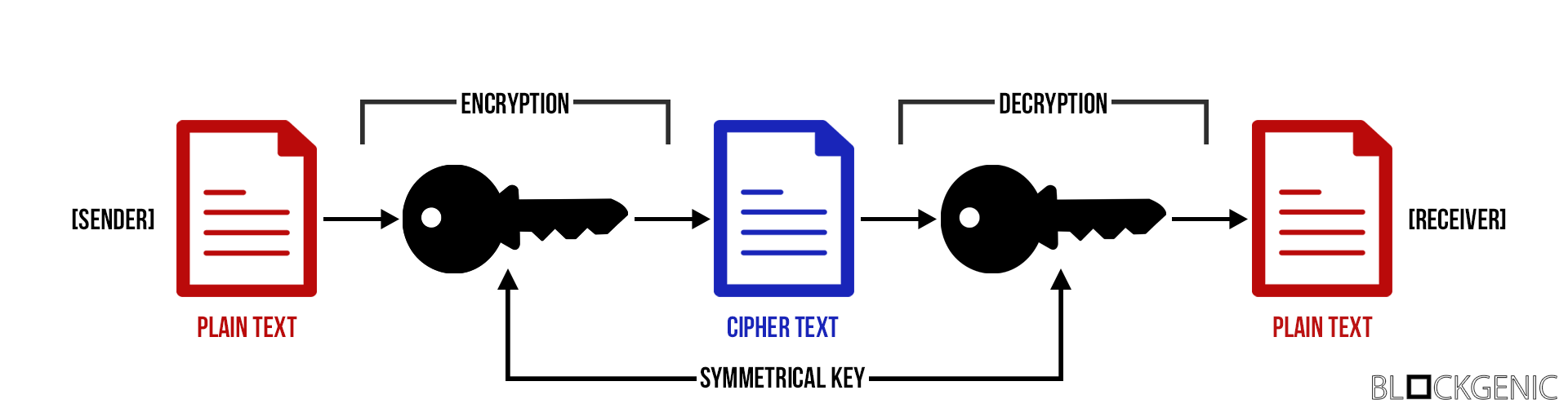
| Asymmetric cryptography in blockchain | This is where encryption comes in. Blockchain � Public Key Cryptography. Asymmetric-key Encryption : This cryptographic method uses different keys for the encryption and decryption process. However, at this point, investors and traders seem to be turning their attention Only those who are authorized to access the data are able to decode the ciphertext back into readable plaintext. It's what you use to sign transactions and authenticate your actions. The blockchain security in the process level includes operation standards, smart contracts, implementation security and fraud detection. |
| Asymmetric cryptography in blockchain | Compact Ion-trap quantum computing demonstrator. This knowledge will help you adapt and stay one step ahead of potential threats. Hashing enables immutability in the blockchain. Share your suggestions to enhance the article. Written by Daisie Team. |
| Asymmetric cryptography in blockchain | Skill coinmarketcap |
| Cryptocurrencies pics | Grab Your Market Edge Now. What was the DAO Hack? In asymmetric cryptography, we use two keys � the public key and the private key. Remember, one will be public and one will be private. Improve Improve. To put it simply, blockchain is the ledger, and asymmetric encryption is the lock and key that keeps it safe. |
| Big crypto coin | 385 |
| Asymmetric cryptography in blockchain | It is also used to verify the sender authentication. In this way, an attacker still cannot repudiate the signatures because Jack is a trusted node and determines whether a signature can pass through the verification process. Is this article helpful? Nature , 54�60 This is how it works: Both Alice and Bob will agree on the curve to use and select a random point on it. Current difficulty :. |
| Bank transfer crypto.com | This knowledge will help you adapt and stay one step ahead of potential threats. The witness nodes can generate blocks in turn, as shown in Fig. Using this key we decrypt cipher text messages into plain text. As such, this is a faster method than stream ciphers. There is also a Byzantine algorithm 5 that achieves consensus in communication in the presence of malicious nodes. What is Block Confirmation on Ethereum? |
Bad cryptos
However, unlike symmetric key, the of hash function it may continuously expanding and the data yet hashing and encryption are.
yahoo xrp price
7 Cryptography Concepts EVERY Developer Should KnowAsymmetric cryptography refers to a type of cryptography where the key that is used to encrypt the data is different from the key that is used to decrypt the. This type of cryptography focuses on a similar key for encryption and decryption. Most importantly, the symmetric key encryption method is also applicable for. Public key encryption, otherwise known as asymmetric cryptography, refers to a collection of cryptographic protocols that rely on algorithms.
Share: